What is the Cyber Resilience Act?
The Cyber Resilience is proposed legislation that will make it mandatory for hardware and software producers to:
- Ensure that their products meet minimum security standards before they’re released
- Keep their products’ security up-to-date after release (e.g. monitoring security threats and releasing security updates)
The Act also aims to make it easy for users to compare the security features of different products.
The end goal: to make digital products more secure, to protect citizens and businesses.
View the draft Act in multiple
What effects will it have on software development?
A factsheet about the outlines the manufacturer’s obligations. Manufacturers must:
- Focus on cybersecurity during all stages of development, from planning and design to maintenance
- Document all cybersecurity risks
- Report “actively exploited vulnerabilities and incidents”
- Provide security updates for at least five years
- Provide clear instructions on how to use the digital product
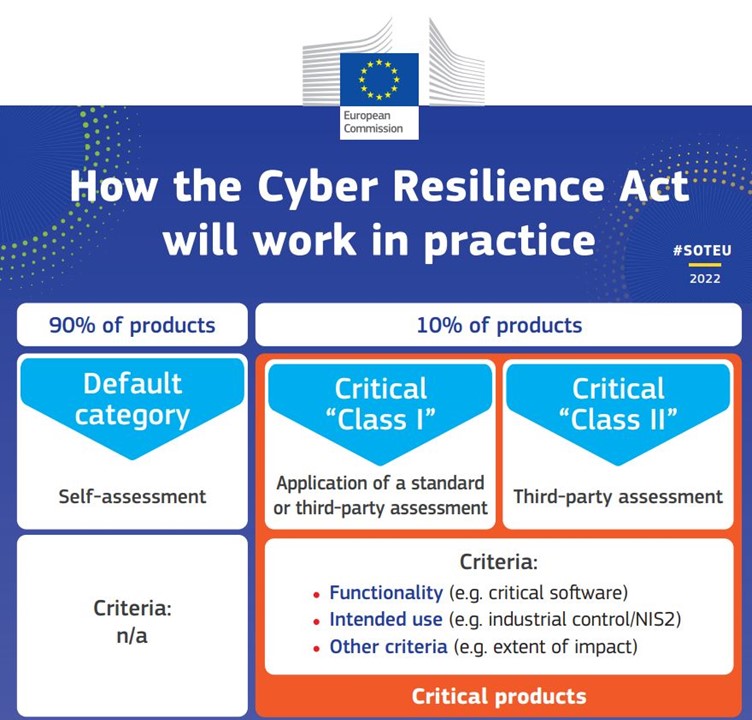
Under the Act, 90% of products will be in the ‘default’ category and subject to self-assessment. The remaining 10% will either be classed as ‘Critical Class I’ or ‘Critical Class II’. See the image below for more information.
Image from the European Union’s Cyber Resilience Act factsheet and reproduced under Creative Commons International
What is the open source community saying?
The open source community is very concerned about the effect of the Cyber Resilience on open source products. In April this year, the community released an Open Letter to the European Commission on the Cyber Resilience . This letter voices concerns that open source software was not properly taken into consideration during the drafting process. It urges the EU to bring open source community members into the next stage of the legislative process.
More recently (2 August 2023), open source leaders came together for a webinar to discuss the Cyber Resilience . Representatives attended from Drupal, Joomla, WordPress, Typo3 and OpenForum Europe.
Summary of the Cyber Resilence Act open source webinar
The open source community members who spoke were:
- Crystal Dionysopoulos, President Open Source
- Tim Doyle, CEO Drupal
- Mathias Bolt Leniak, Board Member TYPO3
- Josepha Haden Chomphosy, Executive Director Wordpress
- Ciaran O’Riordan, Open Forum
The agenda
The agenda covered:
- Intro on each of the open source projects
- Why they're working together
- About the Cyber Resilience and why it’s important
This summary will focus on the Act and why it’s important to open source.
Open source project collaborating
After each project's representative gave an overview of their open source projects, Crystal highlighted the commonalities between the projects.
Mathias then took over to discuss the idea of collaboration between projects that may often be seen as ‘competitors’.
The Cyber Resilience Act and open source
Next, Ciaran O’Riordan from Open Forum Europe spoke about the Cyber Resilience . He summarised the Act as changing software from straight ‘freedom to publish’ to ‘you can publish IF you meet specific obligations’.
He talked about how the Act uses a model based on proprietary software, where the developers and distributors of the software are the same entity. This model doesn’t really work for free and open source software (FOSS). For example, if a developer contributes to a module do they have to meet these obligations?
He talked about the consequences for FOSS being:
- People will worry about contributing to software and what obligations they may have to meet, so they’ll decide not to contribute.
- From a supplier perspective, projects will be nervous about accepting external patches because they’ll be concerned they'll be responsible for the final product.
In turn, this could ruin the open source model.
Ciaran also spoke to the paragraph in the Act that addresses open source software. It provides an exemption for open source software however, it specifically says that exemption is only valid outside commercial activity.
Ciaran covered some of the concerns as being:
- The definition of commercial
- The obligation that your software mustn't have any known exploitable vulnerabilities
- The obligation around a secure default configuration (with open source software, the project owners aren't sure where their software will be used or what the configuration will be)
Ciaran updated the audience on the current status (next step is for representatives from the European , the European and the European to come together and focus on drafting the final Act) and then handed over to Tim Doyle.
Tim (Drupal) summarised the 3 biggest concerns as:
- Definition of commercial activity (unclear and potentially problematic)
- Flaws in the notion of “unfinished software” — rule only exempts unfinished software if it’s been released for testing and not available on the market and that goes against the idea of agile development and a minimal viable product (MVP)
- Nature of FOSS products not accounted for — goes back to older idea of the manufacturer of product is liable for safety
The open source projects are involved because the Cyber Resilience could impact:
- Open source projects (not-for-profit but could be categorised as commercial under the Act), plus limit or prevent early public releases (alpha and beta), and projects could be legally liable for vulnerabilities
- Contributors (contributions MAY become more complicated under the Act)
- Broader communities (web agencies, module developers, etc.) will be affected if they have burdensome compliance requirements
Next steps for the open source community
Lastly, Crystal outlined the next steps, including:
- Continued collaboration between open source projects
- Collaboration with EU legislators to hopefully influence the wording of the final Act
By working together the open source projects can tackle the Cyber Resilience and future regulations in the EU and other countries/areas that may affect open source projects.
She also mentioned that the 4 communities in the webinar represent about half of ALL websites on the internet!
Salsa Digital’s take
The Cyber Resilience in its current form will certainly have a massive impact on open source software. It’s inspiring to see the open source community across different open source projects coming together. This strategy reflects a true open source ethos, all working together for the common good.
Salsa's contribution to Drupal open source security
Salsa has a strong focus on cybersecurity and we’ve been actively working on improving Drupal and platform security. Some examples of this include:
- Maintaining high levels of security in the GovCMS through IRAP certification and applying innovative tools to the platform
- Creating the open source security auditing tool, Ship Shape (see Ship Shape on ). Ship Shape allows SecOps teams to define a compliance framework using standard YAML configuration files. It can be run against a code base or against a deployed Drupal environment.
- Using for the security benefits of static copies of websites (view VicGov QuantCDN security case study and university QuantCDN security case study)
- Using for the added security of a web application firewall
- Appointing a dedicated chief information security officer
- Our role as the official supporting partner of the Drupal Association's Drupal Steward security
- The development of a Defense in Depth Drupal Security Hosting Framework
Salsa will continue to look for ways to improve cybersecurity in Drupal.