About the National Institute of Standards and Technology (NIST)
is a US-based agency that provides critical measurement solutions to promote equitable standards such as the NIST Cybersecurity (NIST CSF). NIST CSF is recognised globally as one of the leading standards for organisational cybersecurity management. The CSF is based on existing standards, guidelines and practices for organisations to better manage and reduce cybersecurity risk. In addition, it was designed to foster risk and cybersecurity management communications among both internal and external organisational stakeholders.
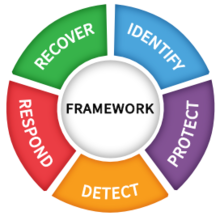
The NIST covers the following five domains:
Identify: Activities to understand and manage cybersecurity risk by identifying assets, vulnerabilities and threats.
Protect: Activities to implement safeguards to mitigate identified risks.
Detect: Activities to identify and detect cybersecurity events promptly.
Respond: Activities to plan for responding to and mitigating cybersecurity incidents when they occur.
Recover: Activities to plan for the recovery and restoration of systems and services after a cybersecurity incident.
A description of each of the NIST domains is detailed below.
NIST CSF: Identify
The “Identify” domain focuses on understanding and managing cybersecurity risk within an organisation by identifying and cataloguing key assets, vulnerabilities and potential threats. This domain provides a foundational understanding of an organisation’s current cybersecurity posture and sets the stage for the development of effective cybersecurity strategies and controls.
The key “Identify” principles include:
Asset management: Identify and inventory all information technology assets, including hardware, software, data and intellectual property.
Vulnerability assessment: Conduct vulnerability assessments to identify weaknesses and vulnerabilities in systems and applications.
Threat assessment: Assess and catalogue potential cybersecurity threats and threat sources.
Risk assessment: Evaluate the potential impact of cybersecurity risks on operations, financial stability, reputation and compliance obligations by an organisation.
Business environment: Consider the organisation’s business context, objectives and regulatory requirements to understand how cybersecurity aligns with its mission and how it impacts business processes and goals.
Governance and policies: Review and establish governance structures, policies and procedures related to cybersecurity risk management.
Asset classification: Classify assets based on their sensitivity, value and criticality, which helps prioritise protection efforts and allocate resources effectively.
Data protection: Identify and protect sensitive data through encryption, access controls and data loss prevention measures.
NIST CSF: Protect
The “Protect” domain focuses on implementing safeguards and security measures to mitigate the risks and vulnerabilities identified in the “Identify” domain. Its primary objective is to establish and maintain proactive defences to protect an organisation's critical assets, systems and data from cybersecurity threats.
The key “Protect” principles include:
Access control: Implement access controls and mechanisms to ensure that only authorised individuals or systems have access to sensitive information and critical systems.
Data security: Data protection measures are put in place to safeguard sensitive information, including encryption, data classification, data loss prevention (DLP) and secure data storage.
Awareness and training: Conduct cybersecurity awareness and training programs to educate employees, contractors and other stakeholders about security policies, procedures and best practices.
Security policies and procedures: Establish and maintain cybersecurity policies and procedures that define the organisation’s expectations for security practices.
Protective technology: Implement security technologies and tools to protect against malware, insider threats and other cybersecurity risks.
Physical security: Implement physical security measures to protect critical infrastructure, data centres and facilities.
Secure configuration management: Establish secure configuration baselines for hardware and software components.
Maintenance and protective processes: Implement procedures for regular system and software maintenance, including patch management, vulnerability management and secure code development practices.
Incident response planning: Develop and maintain an incident response plan that outlines procedures for responding to cybersecurity incidents effectively.
Supply chain risk management: Evaluate and manage cybersecurity risks associated with third-party vendors, suppliers and partners.
Security assessments and continuous monitoring: Regularly assess the effectiveness of security controls through testing, vulnerability assessments and penetration testing, continuously monitoring systems and networks for security anomalies and threats.
NIST CSF: Detect
The “Detect” domain focuses on the timely and effective identification of cybersecurity events and incidents within an organisation’s environment. Its primary objective is to establish the capabilities needed to recognise and detect potential cybersecurity threats as they occur or even before they cause harm.
The key “Detect” principles include:
Anomaly and event detection: Implement mechanisms and tools to monitor and analyse network traffic, system logs and user activities for unusual or suspicious patterns.
Continuous monitoring: Establish continuous monitoring processes to track the security posture of systems and networks in real-time, using capabilities such as intrusion detection systems (IDS), intrusion prevention systems (IPS), and security information and event management (SIEM).
Incident detection: Develop and maintain incident detection procedures and technologies that allow organisations to recognise and categorise cybersecurity incidents promptly.
Security information sharing: Participate in information sharing and collaboration with external organisations.
Incident response: Establish processes and procedures for responding to and mitigating security incidents once they’ve been detected.
Detection automation: Automate the detection of known threats and vulnerabilities by leveraging security technologies like threat intelligence feeds, machine learning and behaviour analysis.
Forensics and analysis: Implement capabilities for conducting cybersecurity forensic analysis to understand the scope, impact and root causes of security incidents.
Vulnerability assessment: Regularly scan and assess systems and applications for known vulnerabilities, including those disclosed in the Common Vulnerabilities and Exposures (CVE) database.
User and entity behaviour analytics (UEBA): Employ UEBA solutions to monitor and analyse user and entity behaviours to detect deviations that may indicate insider threats or compromised accounts.
NIST CSF: Respond
The “Respond” domain focuses on developing and implementing effective response and recovery measures to address and mitigate cybersecurity incidents when they occur. Its primary objective is to ensure that an organisation can respond promptly and efficiently to security incidents to minimise their impact and facilitate recovery.
The key “Respond” principles include:
Incident response plan: Develop and maintain an incident response plan that outlines the organisation’s approach to addressing cybersecurity incidents.
Incident detection and analysis: Establish processes and mechanisms for detecting, analysing, and confirming security incidents.
Incident containment: Implement procedures and actions to contain the impact of a security incident, prevent further damage, and limit the scope of the incident.
Eradication and recovery: Develop strategies for eradicating the root causes of security incidents and recovering affected systems and data.
Communication: Define communication procedures for notifying relevant stakeholders — both internal and external — about the incident, including legal, regulatory and public relations considerations.
Coordination and collaboration: Establish mechanisms for coordinating incident response efforts internally and collaborating with external organisations.
Legal and regulatory reporting: Ensure compliance with legal and regulatory requirements related to incident reporting and data breach notifications.
Lessons learned: Conduct a post-incident review to assess what worked well and what could be improved.
Documentation: Maintain detailed records of incident response activities, including evidence collection, analysis and actions taken.
Public relations: Develop strategies for managing the public image and reputation of the organisation in the event of a high-profile cybersecurity incident.
NIST CSF: Recover
The “Recover” domain focuses on developing and implementing strategies and processes to recover and restore critical systems, services and data after a cybersecurity incident or disruption has occurred. Its primary objective is to ensure that an organisation can promptly and effectively return to normal operations while minimising the impact of the incident.
The key “Recover” principles include:
Recovery planning: Develop and maintain a comprehensive recovery plan that outlines strategies, procedures and resources for restoring affected systems and services.
Improvement actions: Identify and implement improvement actions based on lessons learned from previous incidents and recovery efforts.
Communications: Establish communication plans and procedures for keeping stakeholders — both internal and external — informed throughout the recovery process.
Service and data recovery: Develop strategies for recovering essential services, applications and data.
Coordination and collaboration: Coordinate recovery efforts across teams and departments within the organisation.
Legal and regulatory compliance: Ensure compliance with legal and regulatory requirements related to data breach notifications, reporting, and other obligations during the recovery process.
Insurance and risk financing: Consider the role of cybersecurity insurance and risk financing in managing the financial impact of a cybersecurity incident and supporting recovery efforts.
Documentation: Maintain detailed records of recovery activities, including the actions taken, timelines and outcomes.
Training and awareness: Train employees and stakeholders on their roles and responsibilities during the recovery phase to ensure that staff is aware of the recovery plan and procedures.
NIST CSF and Drupal security
Drupal's security relies not only on the platform itself but also on how it's configured, deployed and maintained. Following the NIST Cybersecurity can help ensure that Drupal-based systems are more resilient to cybersecurity threats and vulnerabilities. Here are some principles and recommendations on how you can improve your Drupal security through the NIST CSF:
Identify (Category 1 — know your assets):
Inventory: Maintain an inventory of all Drupal installations, modules, themes and third-party integrations.
Data classification: Identify and classify sensitive data stored and processed by Drupal.
Asset management: Keep track of servers, databases and other resources used by Drupal.
Protect (Category 2 — secure your assets):
Access control: Implement strong user authentication and authorisation mechanisms in Drupal.
Data protection: Encrypt sensitive data at rest and in transit using appropriate security protocols and encryption standards.
Security configuration: Follow Drupal's best practices for securing the CMS, including regular updates and patch management.
Security awareness and training: Train Drupal administrators and developers on security best practices.
Detect (Category 3 — monitor for anomalies):
Intrusion detection: Set up intrusion detection systems (IDS) and security monitoring tools to detect unusual activities in Drupal's logs and traffic.
Incident response: Develop an incident response plan for Drupal to address security incidents promptly.
Respond (Category 4 — have a response plan):
Incident response: Execute the incident response plan in case of a security breach or incident involving Drupal.
Recovery planning: Develop a recovery plan to minimise downtime and data loss in the event of an incident.
Recover (Category 5 — restore normal operations):
Backup and restore: Implement regular backups of Drupal websites and databases, ensuring data can be restored quickly.
Continuity planning: Develop a business continuity plan for Drupal-based services to ensure a smooth recovery process.
In addition, the following continuous improvement activities are also recommended:
Vulnerability management: Continuously monitor for Drupal vulnerabilities and apply patches promptly.
Security assessments: Conduct periodic security assessments and penetration testing of Drupal websites and applications.
Risk assessment: Regularly assess and update the risk profile of your Drupal deployments.
Supply chain risk management: Assess the security of third-party modules and themes used in Drupal. Only use trusted and well-maintained extensions.
NIST CSF and Salsa’s Drupal Defense in Depth Framework
While Salsa’s Defense in Depth Security Hosting Framework is a multilayer security approach to help keep your Drupal sites secure, amalgamating the NIST within this approach offers several significant benefits to organisations seeking to enhance their cybersecurity posture and manage cybersecurity risk effectively. Some of the key benefits of implementing the NIST CSF across the Drupal Defense in Depth Framework include:
Structured approach to cybersecurity — provides a structured and organised approach to managing cybersecurity risks.
Customisation and adaptability — flexible and adaptable, allowing organisations to customise it to their specific needs, industry requirements and risk profiles.
Common language — provides a common language for discussing cybersecurity within an organisation and with external stakeholders. This fosters better communication and understanding of cybersecurity risks and mitigation strategies.
Risk management — the framework places a strong emphasis on risk management. By identifying, assessing and managing cybersecurity risks, organisations can make informed decisions about resource allocation and risk tolerance.
Compliance guidance — helps organisations meet various regulatory and compliance requirements, as it aligns with many industry-specific regulations and standards.
Improved incident response — guides organisations in developing and enhancing their incident response capabilities.
Continuous improvement — encourages a continuous improvement mindset by promoting regular assessments, reviews and updates to cybersecurity practices.
In summary, implementing the strategies in our Drupal Defence in Depth Framework amalgamated with the NIST actions and recommendations, can significantly enhance your organisation's cyber resilience, enabling it to better withstand and recover from cyberattacks and disruptions, in a constantly evolving cyber threat landscape.

