On this page:
At a glance
2021 - 2022
6 to 9 months
Completed
CivicTheme, Drupal, CKAN, LAGOON
Federal government
Discovery & strategy, Design & user research, Build & migration, Hosting & maintenance
GovTech, Whole of government, Web development
Multidisciplinary teams, Security
Overview
The challenge
A federal agency (that can’t be named for security reasons) was running an outdated portal with a high total cost of ownership. The agency needed a new portal with a very strong security design.
The transformation
Salsa ran a security stream within the overall project to ensure the new platform met security requirements. The security stream included assessment against the ISM controls and the Essential , and implementation of a secure internet gateway and multi-factor authentication.
The outcomes
- Highly secure portal with fully managed content delivery network (CDN) and fully managed next-gen web application firewall (WAF) (formerly Signal Sciences)
- Origin shield
- The service enables origin to only accept traffic from the CDN or a pre-approved IP list, which has passed high level WAF rules
- Enterprise-scale documentation for further security assessment down the track, if required
Full case study
The challenge — an outdated portal
Our federal agency client had a portal with a high cost of ownership and significant functional gaps. A replacement portal was needed. The client needed to be confident in the security design of the new portal, given it manages highly sensitive information.
The transformation — a new, secure portal
Salsa designed a security stream as part of a program of work to deliver the new portal. The security stream borrowed from Salsa’s experience and expertise in securing other large programs/platforms such as Salsa’s role in achieving IRAP certification for GovCMS (see GovCMS — IRAP security accreditation). In fact, the GovCMS platform’s IRAP assessment was leveraged as part of the final ‘authority to operate’ for the portal.
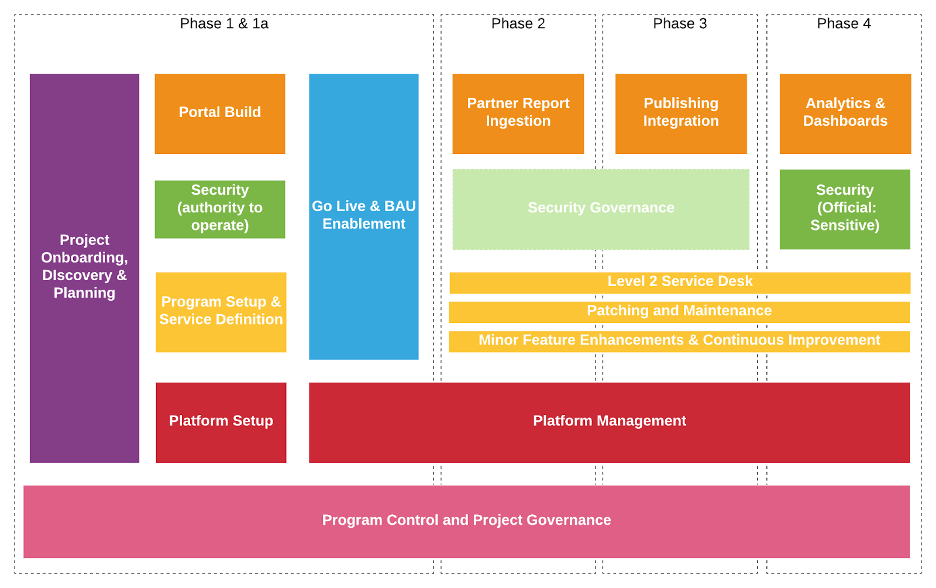
The below diagram shows our streams of work and staged approach for delivering the portal.
The green stream highlights our dedicated security stream, embedded with streams for portal build, service definition, platform setup, and program control and governance.
The challenge of the security stream was to build sufficient confidence for our client’s portal to launch and manage data and content sensitive to Australia's national interests. Salsa’s approach to meet this challenge included:
Use ISM to agree a statement of applicability — The Salsa team assessed the portal’s requirements against ISM September 2021 (see ). All of the ISM 800+ controls were assessed and ranked as applicable or not-applicable and a statement of compliance was included. Salsa then worked with the client’s security team, including the information technology security officer (ITSO) assigned to the project, to agree on the statements of applicability.
Compile action plans for non-compliant controls — A risk-based method of addressing non-compliance was used. When we identified that a particular control was non-compliant, actions to fill the gap were planned and/or the risk accepted with mitigations. The gaps formed an understanding of residual risk.
Invest in a secure internet gateway — One category of non-negotiable controls for the client was the use of a secure internet gateway (SiG) for internet traffic. Many ISM controls, while potentially able to be addressed via means other than a SiG, were more efficiently addressed via the functions of an industry-strength SiG and web application firewall (WAF) solution. Salsa assessed SiG solutions from enterprise SiG providers and chose Signal Sciences. This solution was chosen for: fit to ISM requirements; strength of offering; budget; ease of integration; and timeline to implement given our planned go-live date.
Implement multi-factor authentication (MFA) — Salsa and the federal agency’s security team assessed all ISM controls. Of particular interest and focus were those from the Essential , with MFA for the portal receiving a heightened focus. Salsa implemented an MFA strategy that was customised for portal users. Also an MFA solution needed to meet accessibility criteria, specifically Web Content Accessibility Guidelines (WCAG) 2.1 .
Build the portal with a security-first mindset — The ISM controls assessment identified many requirements that needed to be built for the portal to be appropriately secured, from strong password policies to data retention. Salsa worked with the client’s security team to continually harden the portal.
Independent vulnerability assessment — While the portal didn’t need to be independently ISM/IRAP assessed, the client’s security team and the Salsa team agreed an independent vulnerability assessment was needed to launch the ‘as-built’ system with confidence. An independent third party was engaged to assess the portal and to review technical and process documentation.
Have a system security risk mitigation plan (SSRMP) — Salsa and the client jointly compiled a SSRMP. This plan assessed launch risks and included an action plan to continually address and assess security. The SSRMP formed the basis for the client ITSO to make a recommendation to the federal agency’s executive of ‘authority to operate’. The agency's executive team, in particular its chief information security officer (CISO), granted the authority to operate. We could then plan for the launch.
The outcomes — the portal can confidently manage classified information
The federal agency was able to launch its new portal in May 2022, confident in the portal’s security posture
The security stream provides confidence for ongoing security management and assessment
Enterprise-scale documentation for the platform, processes and tooling enables further security assessment down the track, e.g. full IRAP assessment if that level of accreditation is required
Fully managed CDN
Fully managed next-gen WAF
Origin shield
The service enables origin to only accept traffic from the CDN or a pre-approved IP list, which has passed high level WAF rule.
